A few of the most neglected and most important parts of a Microsoft 365 environment are knowing what type of data you have, where your data goes, and where your data lives. Most people are aware that we can assign sensitivity labels to documents and emails, but we can also assign sensitivity labels to Microsoft 365 Groups, Microsoft Teams, and Microsoft SharePoint sites (known as containers). Applying labels at the container level gives us the ability to override the sharing setting inherited from tenant-level SharePoint sharing setting, set the privacy settings of Teams and Microsoft 365 Groups, and manage the level of access a user has from an unmanaged device.
Let’s say you must build a SharePoint site that will be hosting confidential company data. You have a business requirement that this site must be accessible from anywhere, and any device and must be as secure as possible. Without placing labels on a SharePoint site, these two requirements might have been seen as mutually exclusive. To achieve this requirement, we can apply a default sensitivity label to a site as Confidential/Internal. We can also leverage the power of Entra conditional access rules and restrict access to that site compliant devices. But hold on, you say—our business requirements stated that the site must be accessible from anywhere. Well, enter the label on the SharePoint site. We can now stipulate that non-compliant devices only have web access to the site.
That behavior is a little different from assigning a label to a file or email. There are a few things to keep in mind. First, when you apply a sensitivity label to a supported container, the label automatically applies the sensitivity category and configured protection settings to the site or group. Second, content in these containers does not inherit the labels for the sensitivity category or settings for files and emails, such as content markings and encryption. So that users can label their documents in SharePoint sites or team sites, make sure you’ve enabled sensitivity labels for Office files in SharePoint and OneDrive.
The specific container-level protection settings that are available are as follows:
- Privacy (public or private) of Teams sites and Microsoft 365 groups
- External user access
- External sharing from SharePoint sites
- Access from unmanaged devices
- Authentication contexts
- Default sharing link for a SharePoint site (PowerShell-only configuration)
- Site sharing settings (PowerShell-only configuration)
- Default label for channel meetings
Now that we have the introduction out of the way, let’s discuss how to enable this. Just a reminder: Patience is needed when enabling these features. The settings will take a while (for me about 45 minutes) to sync between Purview and Entra.
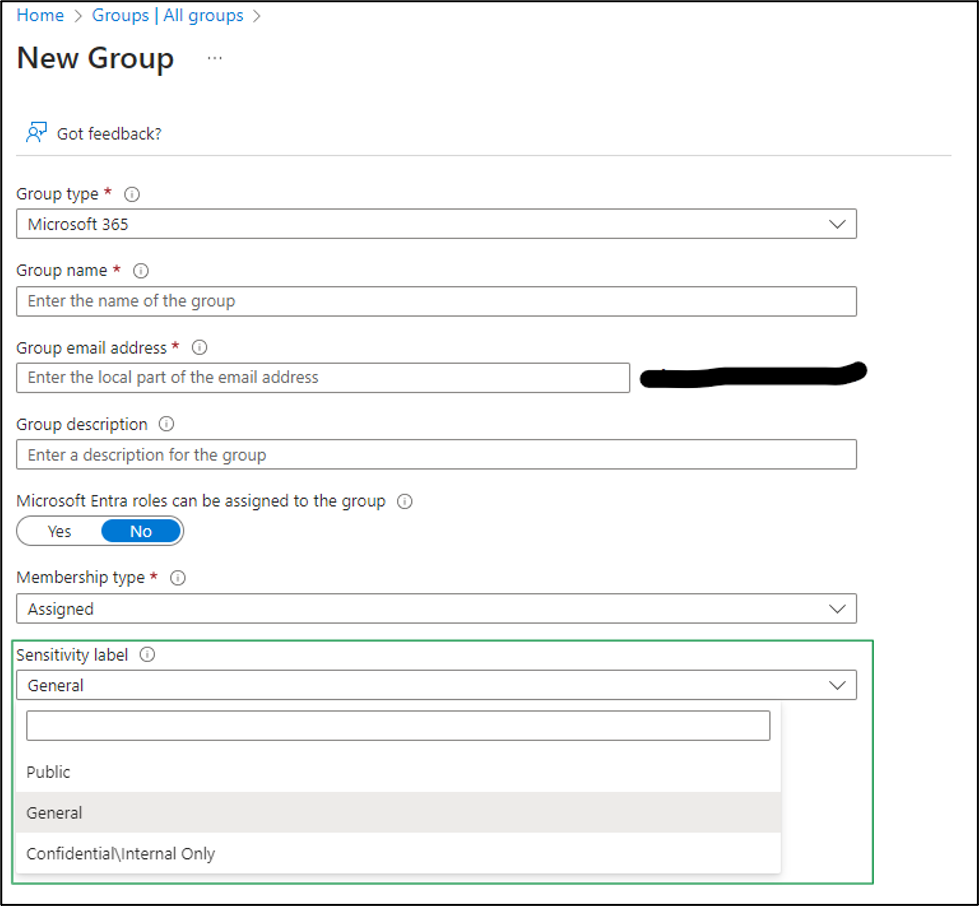
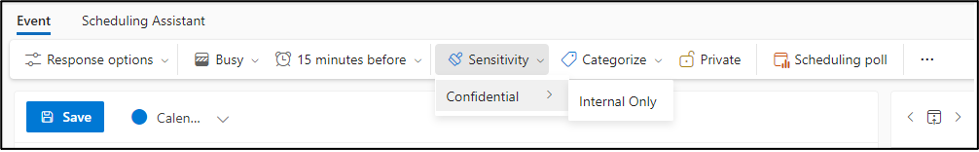
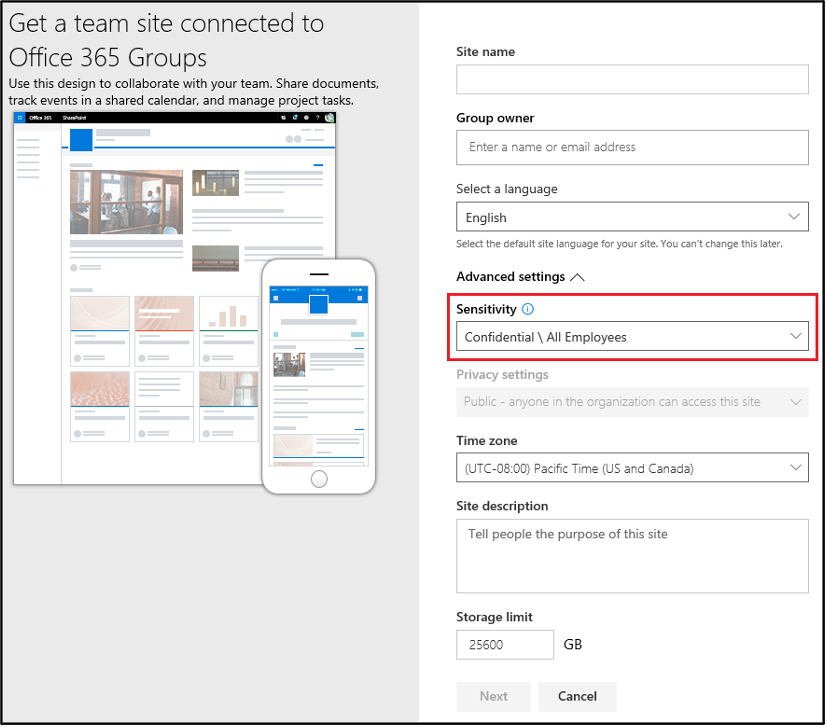
When I enabled this functionality in my tenant, I wanted to test with a different set of labels. Using a new set of labels is not a requirement; you can modify your existing labels to include SharePoint sites, Groups, and Meetings. I decided to build out new labels because I do a lot of testing, and I did not want any cross contamination. The important item for me to test in this scenario was to limit non-compliant machines to web access only. Those settings are reflected in the screenshots below.
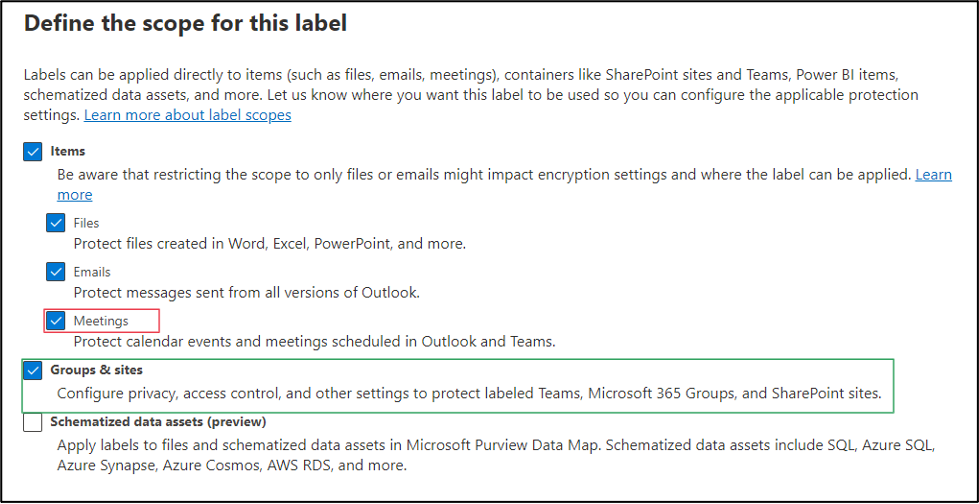
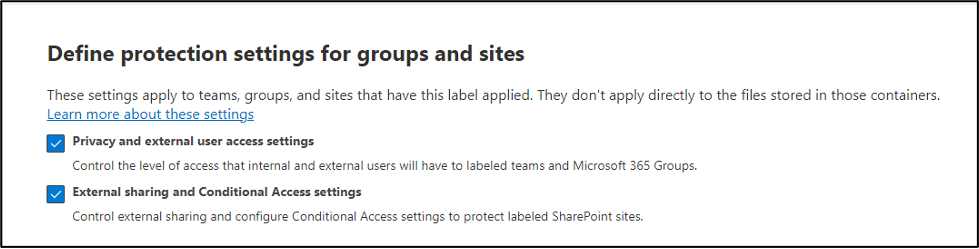
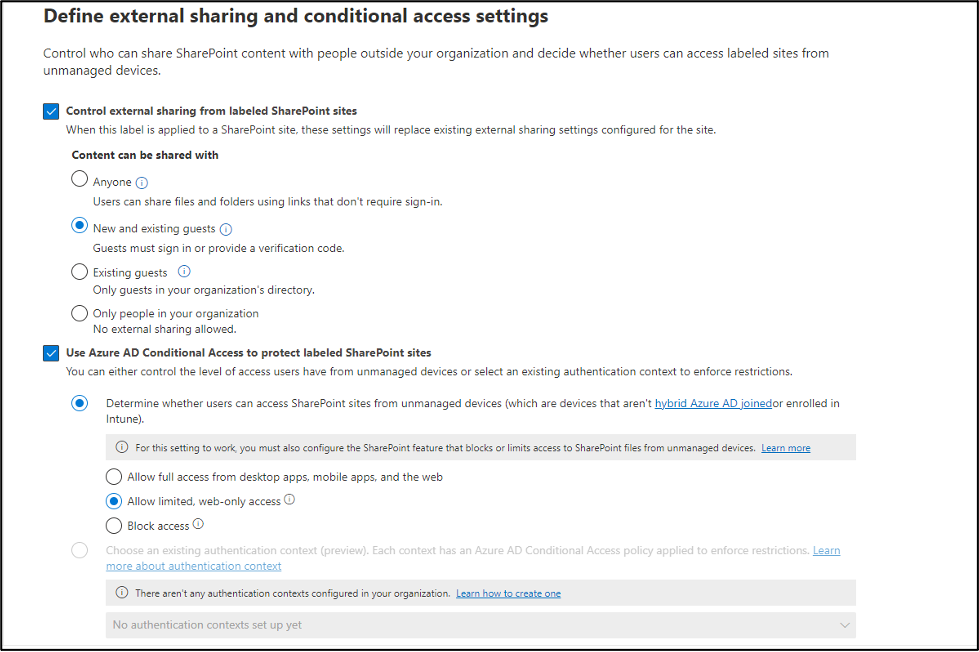
After your labels are created or modified to include Groups and Sites, we need to enable some features in Entra ID. This functionality of this feature leverages Entra ID and requires a minimum of a Microsoft Entra ID P1 license. Because of this dependency, there are a couple PowerShell commands we need to run while connected to Security and Compliance PowerShell. The following commands install the Azure Active Directory (AD) Preview PowerShell module, retrieve the current Entra Unified Group settings, and enable the Microsoft Information Protection Labels setting for Unified Groups at the Org level.
# Step 1: Install and import AzureADPreview module, then connect to Azure AD
Install-Module AzureADPreview
Import-Module AzureADPreview
AzureADPreview\Connect-AzureAD
# Step 2: Get and work with Azure AD Directory settings for Group.Unified
$grpUnifiedSetting = Get-AzureADDirectorySetting | Where-Object -Property DisplayName -Value "Group.Unified" -EQ
$Setting = $grpUnifiedSetting
$grpUnifiedSetting.Values
# Step 3: Enable MIP Labels
$Setting["EnableMIPLabels"] = "True"
# Step 4: Update Azure AD Directory setting
Set-AzureADDirectorySetting -Id $grpUnifiedSetting.Id -DirectorySetting $Setting
We can run the following commands to verify that the value “EnableMIPLabels” is set to true.
# Get Azure AD Directory settings for Group.Unified
$grpUnifiedSetting = Get-AzureADDirectorySetting | Where-Object -Property DisplayName -Value "Group.Unified" -EQ
$grpUnifiedSetting.Values
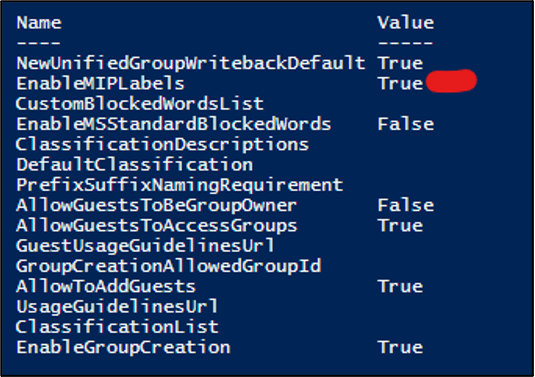
The last step is to synchronize our labels to Entra ID. To do this, we need to connect via PowerShell to the security and compliance center. For reference: Connect-IPPSSession -UserPrincipalName. Once connected, we run the following command: Execute-AzureAdLabelSync. That’s it; now we wait. As mentioned earlier, the synchronization took about 45 minutes for me. The results are shown in the following screenshots.
REFERENCES:
- https://learn.microsoft.com/en-us/purview/sensitivity-labels-teams-groups-sites#enable-this-preview-and-synchronize-labels
- https://learn.microsoft.com/en-us/azure/active-directory/enterprise-users/groups-settings-cmdlets
- https://learn.microsoft.com/en-us/azure/active-directory/enterprise-users/groups-assign-sensitivity-labels

